Difference between revisions of "ADFS 2.0 Relying Party Trust Configuration"
From Joomla! Documentation
m (added Category:Server configurations using HotCat) |
|||
| Line 79: | Line 79: | ||
</li> | </li> | ||
</ul> | </ul> | ||
| + | |||
| + | [[Category:Server configurations]] | ||
Latest revision as of 20:48, 26 May 2013
This document explains how to configure the Relying Party Trust in ADFS 2.0 manually.
Prerequisites
- Relying party identifier
- Token encryption certificate(.crt file)
- WS-Federation Passive redirection URL.
Installation
The below screen captures will show you how to set up the ADFS Relying Party Trust manually.
- ADFS 2.0 Management
Open ADFS 2.0 Management tool from Administrative tools
- Relying Party Trust Wizard
- Select Data Source
Select the option ‘Enter data bout the relying party manually’
- Specify Display Name
Provide the display name for the relying party. This is the friendly name that can be used to quickly identify the relying party in ADFS 2.0 Management Console.
For simplicity, we recommend this to be same as the relying party identifier.
- Choose Profile
Select the option ‘ADFS 2.0 profile’

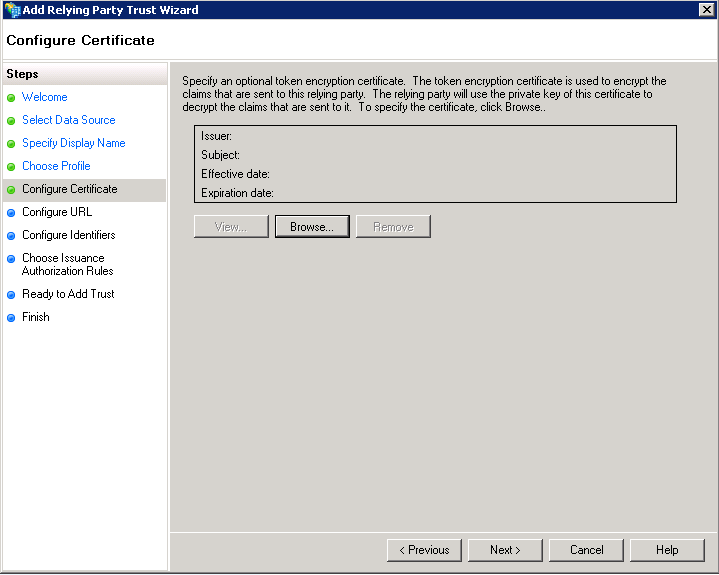
- Configure Certificate - Optional
If you need the response encrypted, please choose your certificate file here.
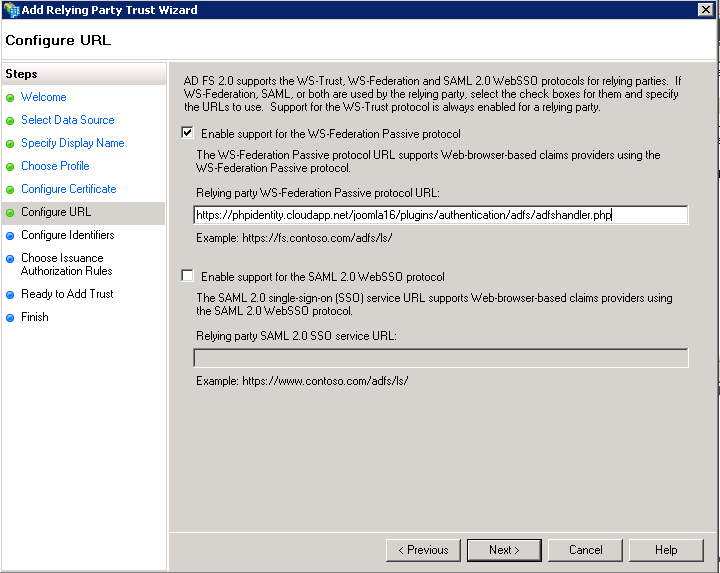
- Configure URL
Configure the WS Federation Passive protocol URL
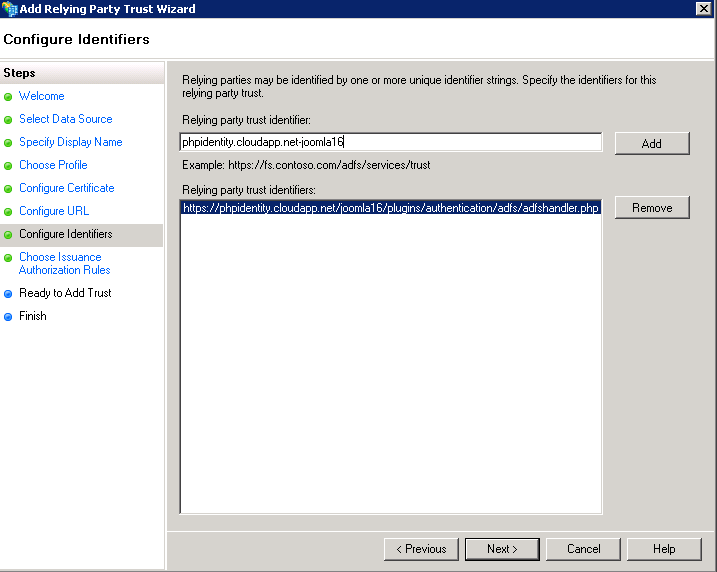
- Configure Identifiers
Configure identifier for relying party
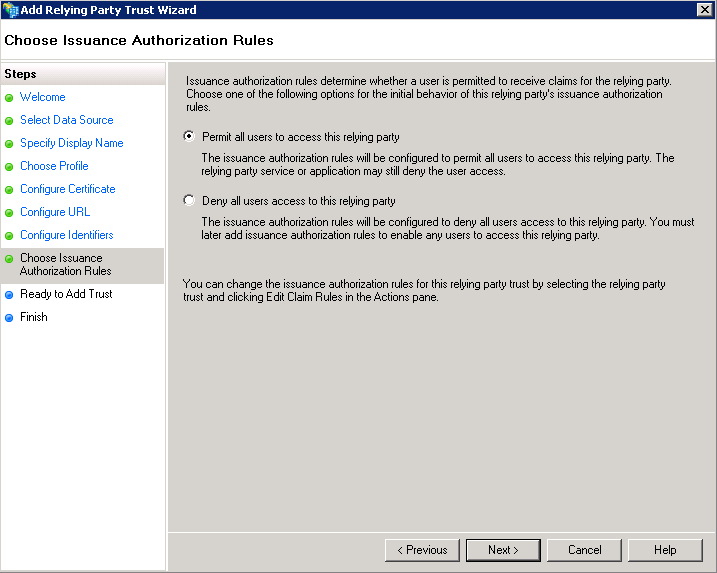
- Choose Issuance Authorization Rules
- Open Claim Rules
After finishing the configuration, you can choose to open the claim rules dialog directly
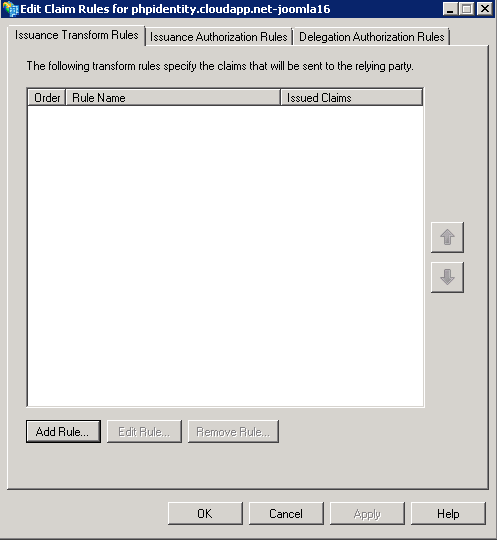
- Edit Claim Rules
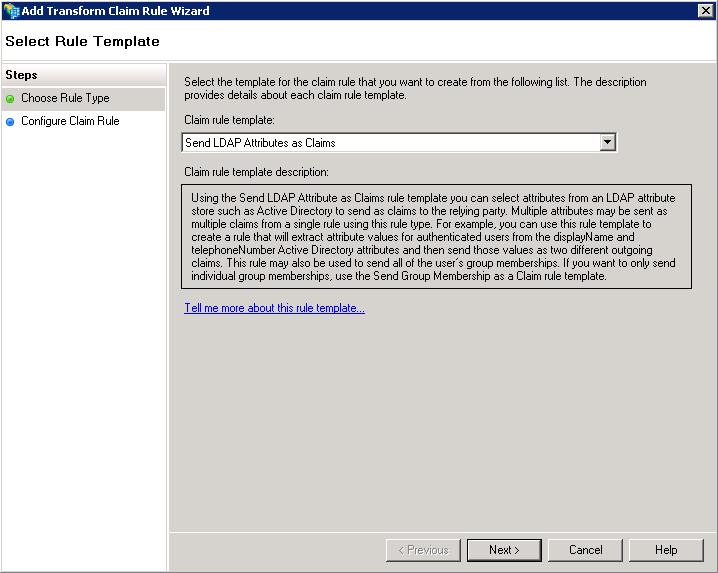
- Select Rule Template
Choose ‘Send LDAP Attributes as Claims’
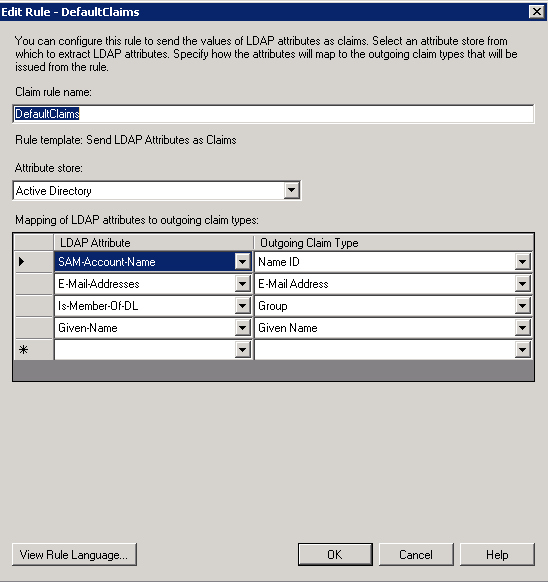
- Edit Rule
Edit the required claims. You need to provide ‘Name ID’ outgoing claim type as mandatory
Known Limitations
- Current solution is tested for keys with 1024 size. This might show you a warning while configuring the certificate.
References
- Configure Relying Party Trust Manually
- Open SSL Commands to create test certificates
- openssl genrsa -des3 -out adfs-simplesaml.key 1024
- openssl rsa -in adfs-simplesaml.key -out adfs-simplesaml.pem
- openssl req -new -key adfs-simplesaml.key -out adfs-simplesaml.csr
- openssl x509 -req -in adfs-simplesaml.csr -signkey adfs-simplesaml.key -out adfs-simplesaml.crt